1. kubernetes dashboard
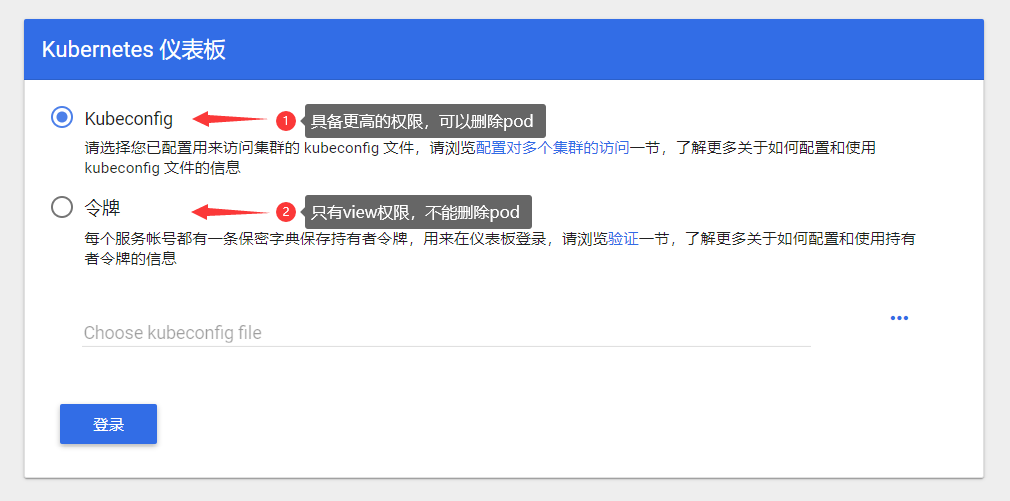
kubernetes dashboard提供了两种登录方式:
- kubeconfig
- 令牌
下面将对这两种登录方式进行介绍。
 |
|---|
| 图1-1 kubernetes dashboard的登录界面 |
1.1 令牌登录
令牌登录就是使用serviceAccount账户的token值登录,在kubernetes中,每个serviceAccount(简称sa)账户都对应一个token值,我们就可以使用该值进行登录。需要注意的是,使用token登录只具有view权限,不能在dashboard中删除或创建pod。
1 | ############################################### |
1.2 kubeconfig登录
kubeconfig文件就是kubect登录使用的验证文件, 一般位于~/.kube/config。如果没有的话需要使用kubectl config命令生成,这里不再详细介绍。
获取kubeconfig文件内容
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20$ kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.0.3:6443
name: cluster.local
contexts:
- context:
cluster: cluster.local
user: kubernetes-admin
name: kubernetes-admin@cluster.local
current-context: kubernetes-admin@cluster.local
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
获取sa账户token
1
2
3
4
5
6
7
8
9
10
11
12###############################################
# 查看sa账户
###############################################
$ kubectl get sa
NAME SECRETS AGE
default 1 38d
###############################################
# 查看default账户的secret
###############################################
$ kubectl describe secret default | awk '$1=="token:"{print $2}'
eyJhbGciOiJSUzI1NiIsImtpZCI6ImVUYzFjVUhDeUJqeXNzcnpJUEpfaGpWVnhyOS1TVXV2REZEYjBTazA3NzAifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZmF1bHQtdG9rZW4tajI3ZjIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmYXVsdCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImFjOWE3NjY1LTk3ZmEtNDk1MC05NjBlLTIxNThkNWFiOWMwYSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQifQ.IJYDGgXRrH--GRiiz2P18RyozsjvIsLIwxVO7azfCUPkjeyjSIwbUrlH75Uxo3LXrQvvSKMKnJOyPovQ7K_zV3Ot0ufjjsoM3IZe3LZllr09JR70AvJkdckXjRnK7QeKoZRJNVKQt45emRCd9PKCbc8m8u3pianRwJWlPBXCTa-uyxWbsgoKXJXBD2HvgkphPDTLKjYQKPvvh6nSs2vfvX2MPaG98njY6F27W-1YFchgo_df3rFS-SoMlXVlizJsjOV-vr1Kye6EFGBI33fHXFCkCxaHE2cpmFtD_bbHZEHK8BdPXT5a5ER19ODlbtPZ8r3ngk8eWqpaSebHv2wWIg
向kubeconfig文件中添加token
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.0.3:6443
name: cluster.local
contexts:
- context:
cluster: cluster.local
user: kubernetes-admin
name: kubernetes-admin@cluster.local
current-context: kubernetes-admin@cluster.local
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImVUYzFjVUhDeUJqeXNzcnpJUEpfaGpWVnhyOS1TVXV2REZEYjBTazA3NzAifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkZWZhdWx0LXRva2VuLTJnNTZ6Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImRlZmF1bHQiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI3M2M1NjI1Yi1mYWJkLTQzZTUtYjY5Ny0yMWY4MDQ2MDg2YTUiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZS1zeXN0ZW06ZGVmYXVsdCJ9.Oh9HH5n2QswxakCiBalXyg71P2VMv_CG5NMjmFyK6Fj_gVnUxsIRGNV3z08QMMVE-d3ZyWP-N8xL-MX2aFyoxV4XwjcJh0c8WYMdVdTQzDBJoAf7x9xbI2faduMIrb1c2WgbF74PMRS8yufR3WlSERySDgWWJnhyLvdiNN0HNoS2J2o72AounyXOD5O0GLiKSZujAUV7HH_6pLZ_W6bGlJjMzma68OLlN5sWoikAhHP1MdbwBVpPbMhnl5cbP4rg5Hs_cMr6Wlhw9j2Mi7CGnYI3JVop23ESwoAJmqNX-5ANQ6015KVBmP7_l9_qIikVSCtP9cTErK9gqXQD90YQ3g
- 角色绑定(如果不执行登录后会提示权限不足),即将sa和role进行绑定
1 | $ kubectl create clusterrolebinding add-on-cluster-admin --clusterrole=cluster-admin --serviceaccount=default:default |
- 使用kubeconfig文件进行登录
附录
最后贴一下kubernetes dashboard的部署文件(基于kubernetesui/dashboard:v2.0.0-beta8)。
1 | # Copyright 2017 The Kubernetes Authors. |
